Burp Suite has been my favorite web app testing tool for a while and seems like it keeps getting better with age & updates. Typically, I have avoided using other tools to parse the Burp output (xml) because most of what we report comes from manual testing. Somewhat recently, I started using extensions to add the manual testing results to Burp and thus it made sense to write a script to parse Burp xml output. Say hello to “breathmint”.
Continue reading
DEF CON 27 has come and gone, and it was amazing to see folks get engaged with the badge, solving the challenges, having fun with the honeypots. We received lots of great feedback, and folks were very curious about the honeypot data. We had great conversations about what hacking actually happens at DEF CON, what kind of hacking can be expected, and we think there is enough evidence to at least partially answer that question. This post is going to serve as a bit of a wrap-up and post mortem. There were a few hidden Easter eggs thrown in during the development of the badge; those are explained below and, of course, a wrap-up of the on-badge challenges.
Note: For the initial post providing an overview of the features and functions of the DEF CON 27 Blue Team Village Badge overview, please visit Part 1 of 2
Continue reading
Integrating Compliance Auditing with DevSecOps
By now you have probably at least read about the benefits of merging development, security, and operations into a cohesive unit (if not also implemented to some degree). Now it’s time to take it a little further: integrating security compliance audits. Whether you face mandated audits, like PCI, FISMA and agency specific implementations like Security Controls Testing (SCA) or NISTIR 8011 flavored Adaptive Capabilities Testing (ACT), or self-imposed assessments for your own [good] reasons (or both), integrating an external audit with your system development and maintenance process can help your organization more efficiently remediate vulnerabilities and weaknesses, and the overall audit process will be less costly.
Continue reading
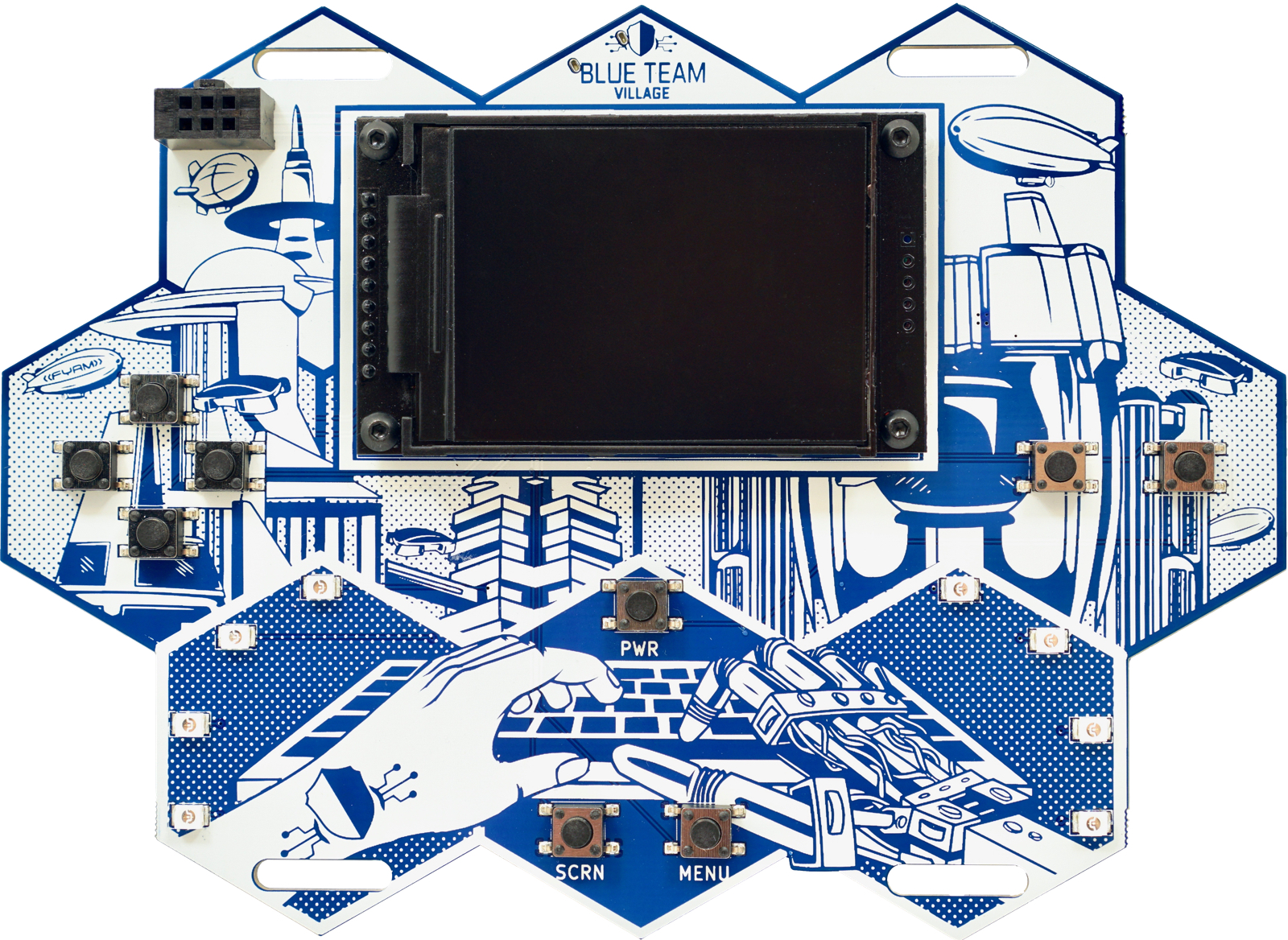
This post is part 1 of 2. Visit Part 2 of 2 for spoilers and behind the scenes info.
With the wave of low-cost PCBs and components, electronic conference badges are now pervasive. I decided to deviate a bit from our usual offensive security focus, have a little fun and build a mobile AP and honeypot which has now evolved to the DEF CON 27 Blue Team Village badge.
This is a short history and overview of the badge, which has been in the works for the better part of a year. The irony is not lost that while my focus most of this century has been on the offensive side of security, that this project has resulted in the official badge for the.. Blue Team Village. This page will be vague at times, as things are still in development and also to leave a few surprises for those who obtain a badge. However, it will be updated with additional information as we get closer to the conference.
Background
The idea for this badge started just before DEF CON 26, when I turned a small Linux based computer into a portable WIFI AP, with always-on VPN, network-wide ad blocking and an LCD screen for simple configuration. The goal was to serve as an AP that would provide VPN access to connected hosts while in a “hostile” (i.e. untrusted, hotel, airport, etc) environment. However, we were not very far away from adding honeypot functionality, so that was implemented on the plane ride on the way over to DEF CON 26, as is tradition. At this point, the devices had two modes, protected AP mode and honeypot mode. However, it wasn’t quite as portable as a wearable electronic conference badge. Thus, after a painstakingly large number of prototypes and revisions, the device slowly became more portable and evolved into a single PCB with screen, quite suitable for an electronic badge.
Continue reading
Having a vulnerability management tool like Tenable Security Center is great. They offer a lot of functionality to analyze, track, and report on the current and past state of systems in the environment. But sometimes that’s overkill. Sometimes you want something quick and easy. Hence we wrote a quick little python script that parses one or more .nessus files and produces a spreadsheet (Excel format). There are five worksheets in the workbook output file:
Continue reading
After the rules of engagement are finalized but before we actually start a penetration test, we perform no-touch reconnaissance or “recon”, all without sending a single packet to our target organization’s environment. The goal is to identify all the in scope assets and data exposures, as the more coverage we attain of a target environment the more thorough we can be with our penetration testing. This information can include things like ip addresses, subdomains, code repositories, employee data or anything that tells us more about the company and introduces a crack in the external defenses. Whether a development server was stood up with an obscure subdomain name, an employee committed credentials to a public Github repository, or a sysadmin posted server logs to Pastebin, our goal is to find these exposures and assess potential risk to an environment before an attacker does.
Continue reading
For a period of time, it was possible to read snippets of memory on a screen-locked mac OS system from the USB port.
A while back we noticed some interesting files created by macOS when inserting a USB drive. These files were related to Spotlight, macOS’s built-in search functionality which indexes and enables searching of files on the system, among other things. The presence of the files is fairly standard, as an invisible /Volumes/<Volume Name>/.Spotlight-V100/ directory are added to every USB drive inserted into a macOS system when Spotlight indexes the files on that drive. However, while analyzing some of the file contents, it appeared that content from several emails (subject lines, email addresses, snippets of message contents) was stored among this data, specifically in the .store.db file which serves as Spotlight’s metadata store. This was alarming as this email data had never been purposely stored on that USB drive. The implications were obviously pretty big. Sensitive data from a macOS system could be inadvertently leaked to a removable USB drive by the OS and potentially exposed without a user’s knowledge.
Continue reading
I will be co-presenting [“Getting Social with the Smart Grid”] (https://defcon.org/html/defcon-18/dc-18-speakers.html#Morehouse) at this year’s DEF CON in Las Vegas.
Littered with endless threats and vulnerabilities surrounding both social networking and the Smart Grid, the marriage of these two technologies is official, despite protests by the security community. Consumers love it because they can brag to their friends about how green they are. Businesses love it more because it provides fresh material for their marketing departments. Hackers love it the most because it opens up attack vectors, both new and old.
Continue reading
As an industry, we have failed. Miserably. Cyber security professionals have implemented a broken methodology and graduated from failing to properly identify the problem to failing to present an effective solution. The network security methodology of: 1. Find Vulnerabilities, and then 2. Apply Security Patch, simply does not work for the custom web application environment. This statement may seem obvious, but it’s exactly what the industry has tried to do.
Continue reading


