DEF CON 27 Blue Team Village Badge Wrap Up
Note: For the initial post providing an overview of the features and functions of the DEF CON 27 Blue Team Village Badge overview, please visit Part 1 of 2
Note: For the initial post providing an overview of the features and functions of the DEF CON 27 Blue Team Village Badge overview, please visit Part 1 of 2
Last Updated: 2019-10-10
This post is part 1 of 2. Visit Part 2 of 2 for spoilers and behind the scenes info.
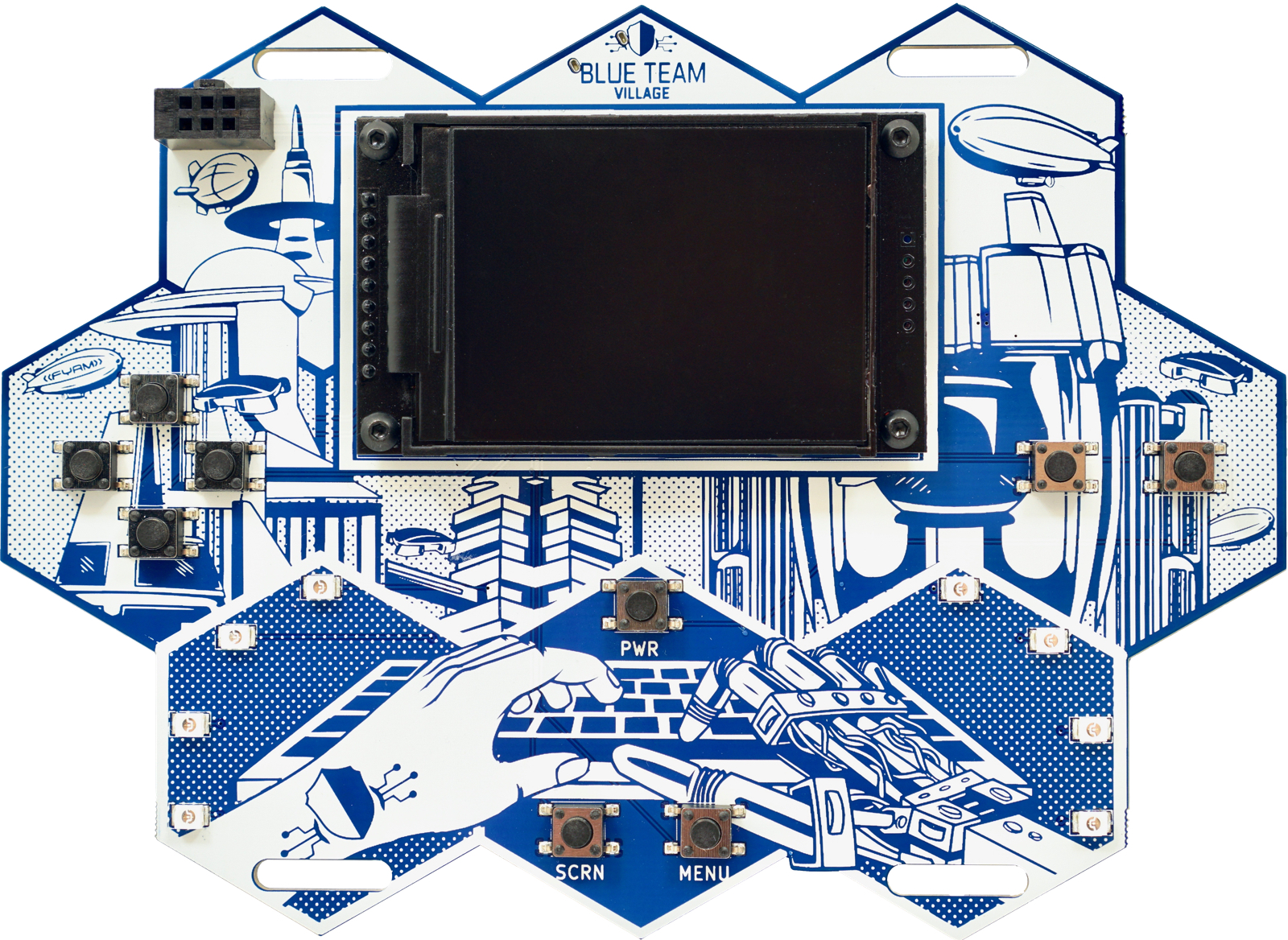
This is a short history and overview of the badge, which has been in the works for the better part of a year. The irony is not lost that while my focus most of this century has been on the offensive side of security, that this project has resulted in the official badge for the.. Blue Team Village. This page will be vague at times, as things are still in development and also to leave a few surprises for those who obtain a badge. However, it will be updated with additional information as we get closer to the conference.
The idea for this badge started just before DEF CON 26, when I turned a small Linux based computer into a portable WIFI AP, with always-on VPN, network-wide ad blocking and an LCD screen for simple configuration. The goal was to serve as an AP that would provide VPN access to connected hosts while in a “hostile” (i.e. untrusted, hotel, airport, etc) environment. However, we were not very far away from adding honeypot functionality, so that was implemented on the plane ride on the way over to DEF CON 26, as is tradition. At this point, the devices had two modes, protected AP mode and honeypot mode. However, it wasn’t quite as portable as a wearable electronic conference badge. Thus, after a painstakingly large number of prototypes and revisions, the device slowly became more portable and evolved into a single PCB with screen, quite suitable for an electronic badge.